@condret I put the original link in the alt text.
@condret Hopefully a screen reader can follow that.
I don't mind having security in everything. It's just that that security should not come at the expense of freedom.
Someone needs to make a fork of @GrapheneOS or #DivestOS which focusses more on other goals, such as freedom and usability, without sacrificing sacurity.
(I've never used DIvest btw. I just mentioned it because it focuses on security as well. Maybe I shouldn't have.)
- replies
- 0
- announces
- 0
- likes
- 0
Anyway, it's a moot point for me because https://social.fbxl.net/objects/56c40baf-43bf-4d87-a705-9a962e1a43f9
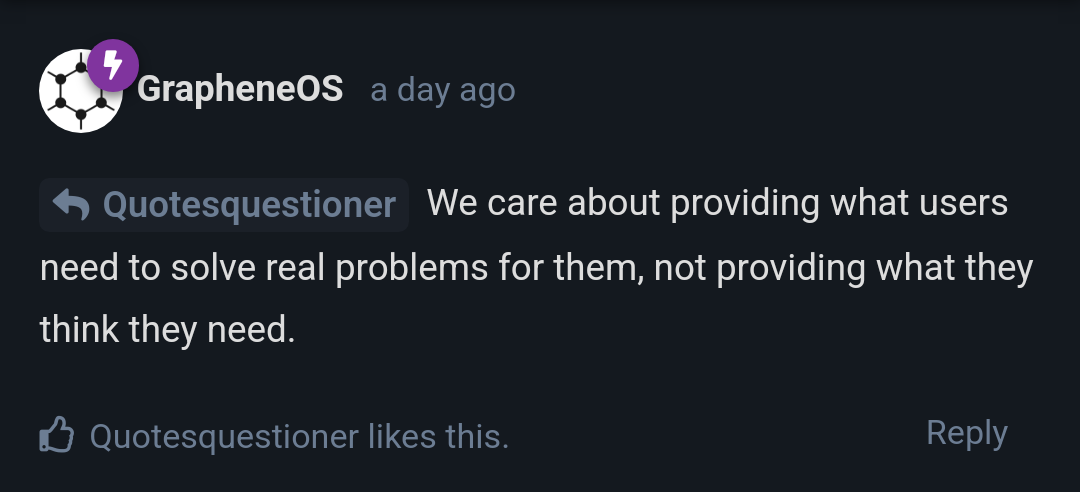
Has it ever occurred to you that not every feature is a privacy or security feature?
From what I can see, the OP just wanted to be able to "share VPN with hotspot devices" because "my tethered device can't easily add a VPN".
I think if you cared a bit more about quality-of-life and usability, more people would want to use it.
But of course, it's your project(TM), and I don't have a say because I don't contribute to it.
Which is fine. Like I said, I don't seem have a working phone anymore. So I have no reason to care.
From what I can see, the OP just wanted to be able to "share VPN with hotspot devices" because "my tethered device can't easily add a VPN".
I think if you cared a bit more about quality-of-life and usability, more people would want to use it.
But of course, it's your project(TM), and I don't have a say because I don't contribute to it.
Which is fine. Like I said, I don't seem have a working phone anymore. So I have no reason to care.
What if they are not using the VPN for privacy? Say, censorship circumvention, or georestriction evasion.
>Why should people who aren't experts or doing any work decide on what to do?
Because users, who in many cases rely on the software for important things, are stakeholders.
But of course, it's completely up to you what governance structure you have.
Because users, who in many cases rely on the software for important things, are stakeholders.
But of course, it's completely up to you what governance structure you have.